UNMATCHED, UNLIMITED VISIBILITY
Introducing 360° Pure-Play Extended Detection and Response ZTN SOC.

Cloud
HuntingMulti-vendor sensor telemetry in search of suspicious threat behaviors, allowing threat hunters to locate and take action to secure cloud infrastructure and secure running workloads wherever they are deployed.Network
InvestigationHuman-machine teaming correlates all relevant threat information and applies situational network security context to more quickly reduce signal from noise and assist with the identification of root cause.Endpoint
DetectionIdentify more and meaningful threats by combining endpoint telemetry with a growing list of security controls providers as well security events collected and analyzed by silent sensors.CROSS PLATFORM
LIGHTWEIGHT SENSORS, SCALABLE, INSTANT DEPLOYMENT, API INTEGRATION
SAAS, HYBRID, ON-PREMISE
Tour the Platform+
Experience World-Class 24/7 Cloud Native SOC
What Results are you looking for?
Consumption-based monthly billing.
Evaluation by nodes. not bytes.
Detection and response in minutes. Not days.
-
RESILIENCE
-
Make business disruption-proof
Be More Resilient
Provides better resiliency to prepare, respond, and recover and defend itself against cyber attacks, limit the effects of a security incident, and guarantee the continuity of its operation during and after the attack.
-
SOC MATURITY
-
Shift from reactive to proactive model
Improve Your Existing SOC
Adapt a new mindset reduce the amount of time it takes to detect and respond to a cyber threat & investigate on persistent attacks.Manage and respond to endless alarms at machine speeds with advanced Automation & Orchestration.We are applying the military’s perspective on cyber security to enterprise security.
-
CYBER SKILLS
-
Cyber security talent crunch
Stop Alert Fatigue And Burnout
Expert Human analysts with skills on modern advanced military grade tools to quickly identify, prioritize, and respond to security incidents & Investigate any suspicious behavior, no matter the time of day.Our SOC security teams have extensive experience with cyber defense operations.
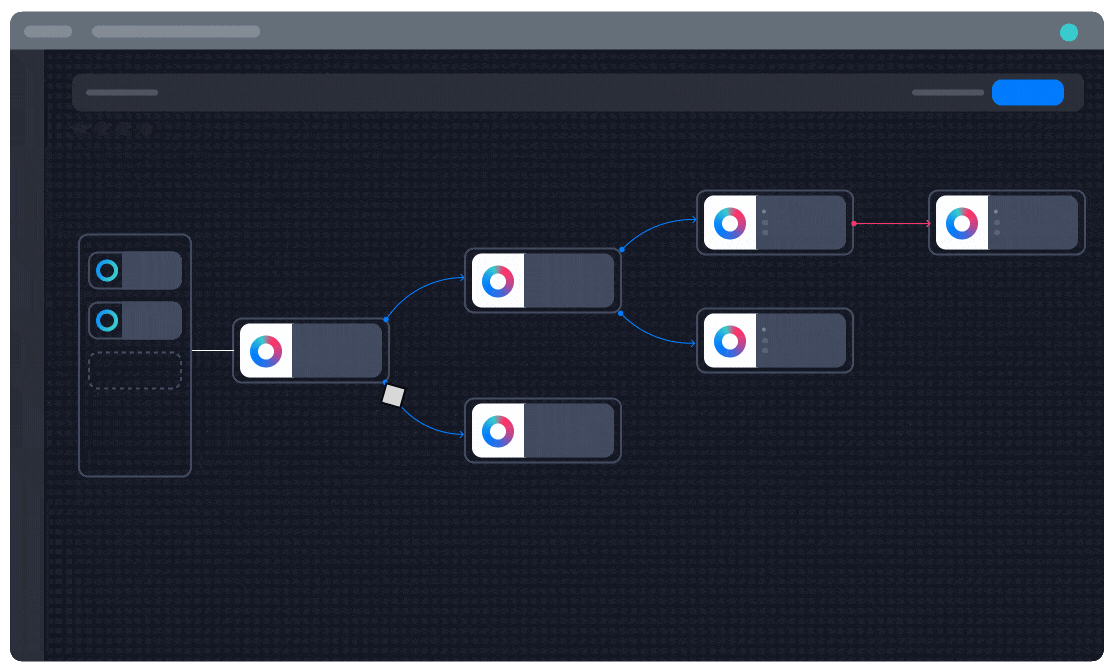
Get Ahead of Adversaries
Tracelay modern future-ready advanced monitoring services with threat intelligence-led approach.SOC powered by XDR brings a proactive approach to threat detection and response that delivers visibility into data across networks, clouds and endpoints to manage next-generation cyber attacks.
We also automatically enrich our Visibility with additional data sourced from network traffic, user information, and third party threat feeds to provide analysts with greater context to investigate and respond to incidents.
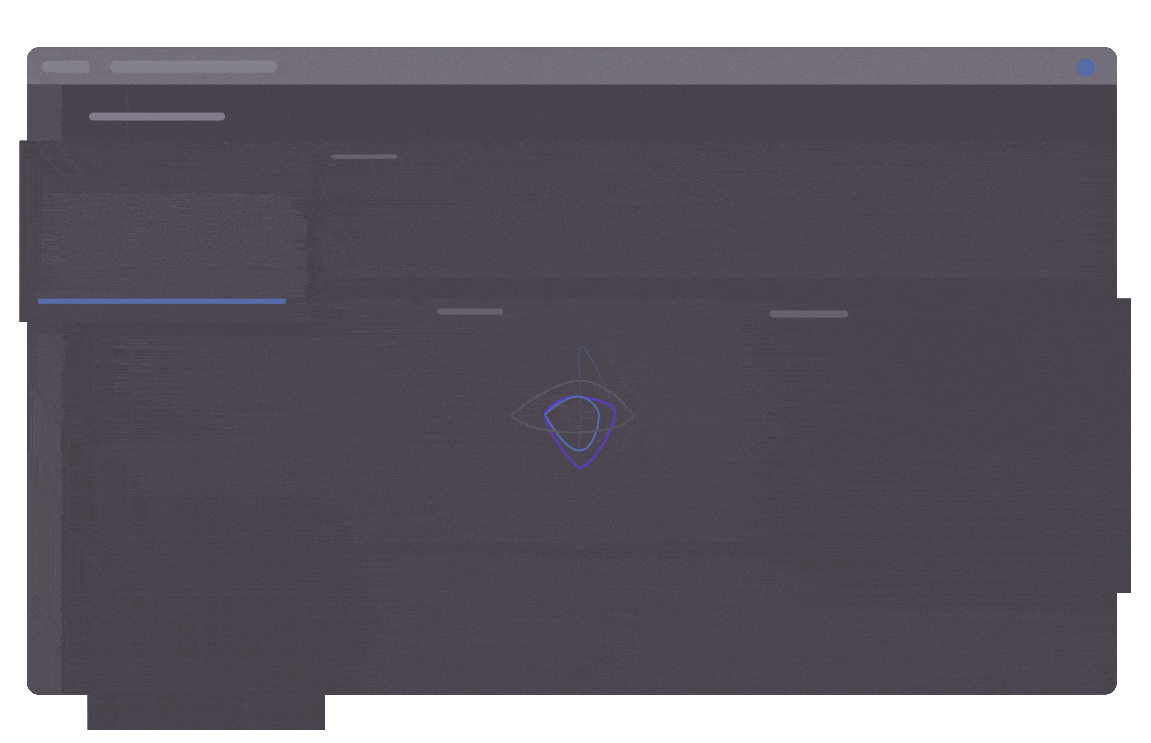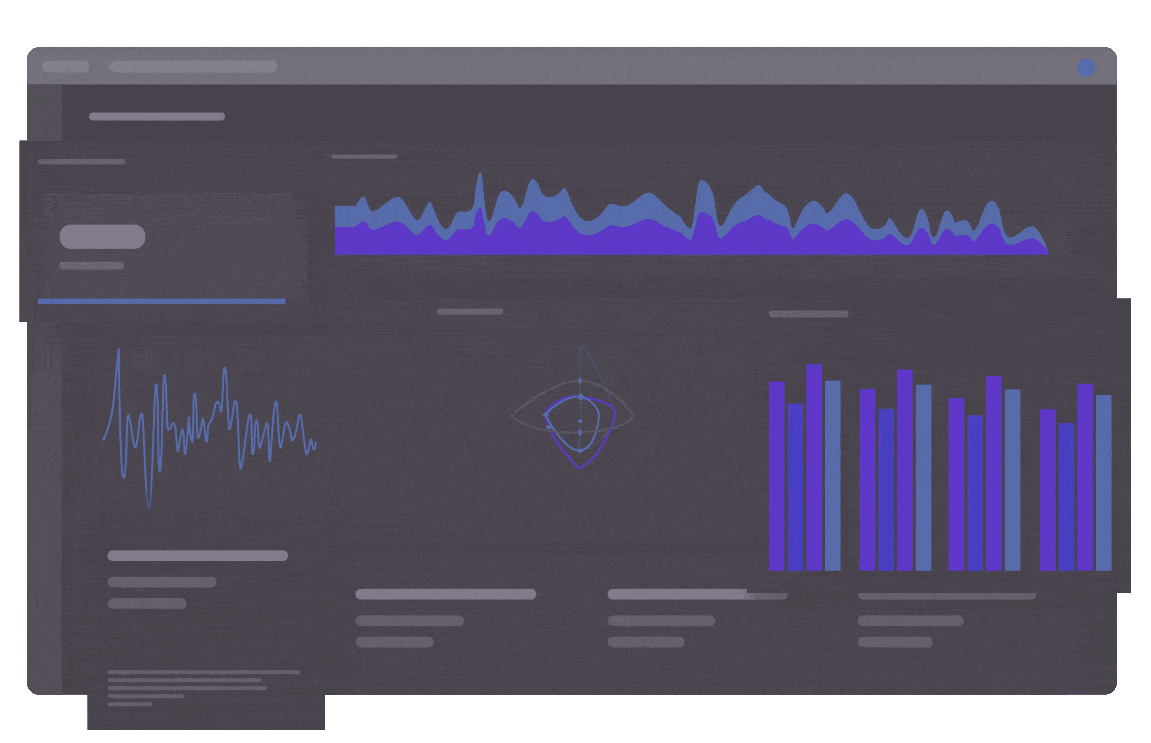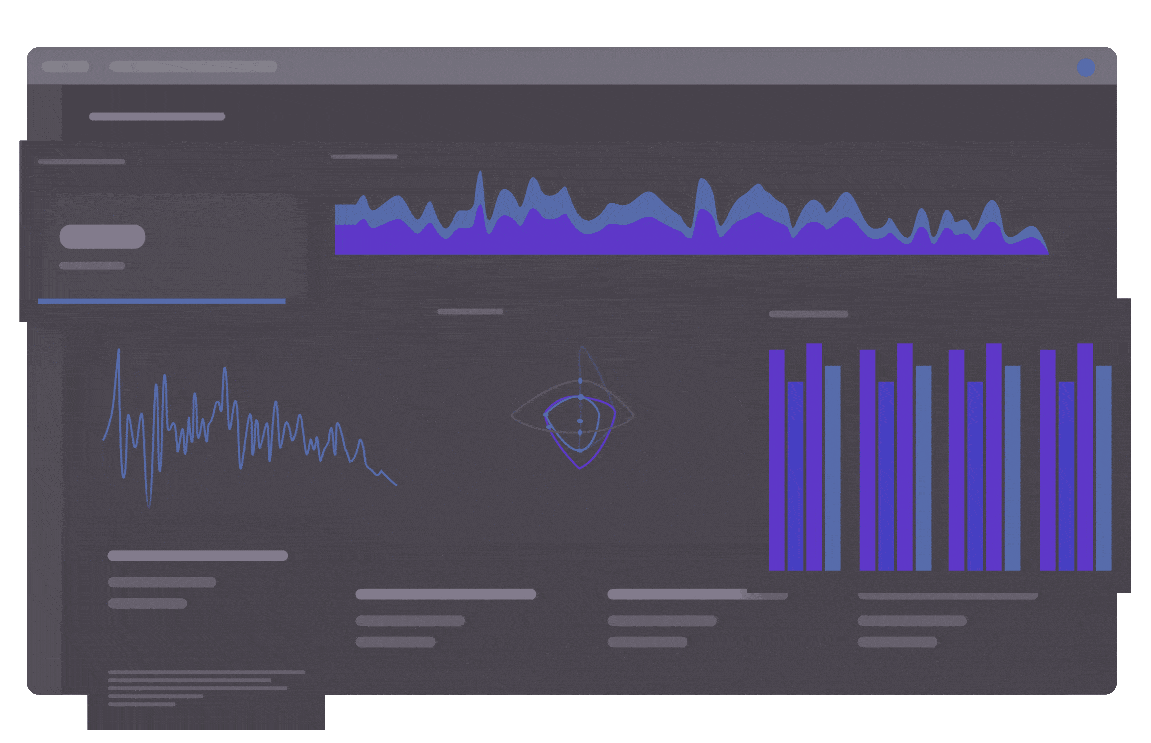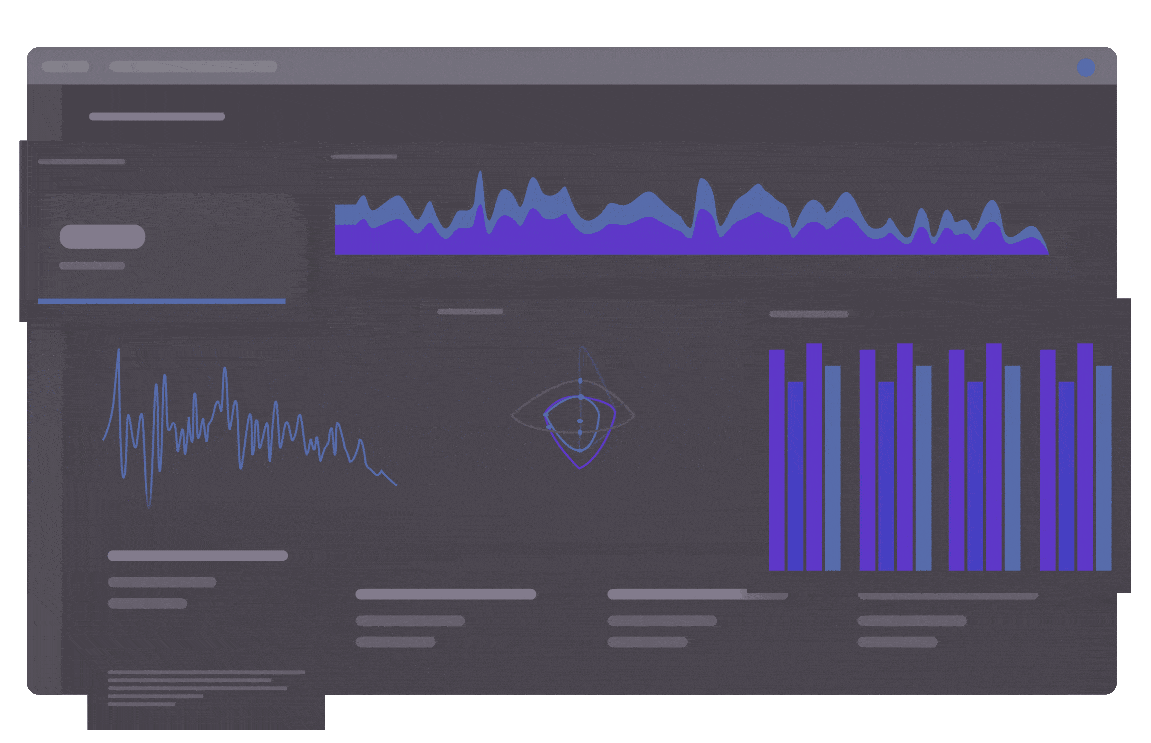
Modern Analyst Monitoring Dashboard
Modern enterprise user interface and workflow designed for simplicity and ease of use for our security analysts.
Analysts can also perform powerful full text searches against all of their non-normalized data to acquire deeper context on what else a particular user, entity, application, or process is doing across the enterprise and cloud environments.